Game 6: Hacknet
- Plays All The Things

- Jul 15, 2025
- 9 min read
Updated: Aug 1, 2025
I am not a cybersecurity expert, but I think the main problem with trying to make anything online secure is that you have relatively few entities that make and maintain locks, and they are severely outnumbered by the many entities that are trying to break through those locks. Today we'll get to pretend to be one of the latter in Hacknet, a 'terminal-based' hacking simulator.
I have a 'To Play' list of games which is a mix of games that I either obtained on sale and haven't played yet, or played for a bit and either didn't finish, or I did finish and want to play again. There are about 140 games currently on the list, which is an indication that I should stop adding to that list, but that resolution doesn't tend to survive the next Steam sale. Anyway, a couple years ago I played Hacknet for several hours but I don't remember much, so we're starting a new game of it.
To finish the tutorial, I need to find the tutorial's process ID and kill it (which is something you can do on a real Unix / Linux system). The game encourages you to 'hack' via unix-style commands that you type in. There's also a graphical interface but not all commands are available by using it so typing is mandatory.

I've been contacted by 'Bit', who wants me to start by getting some programs from Viper's computer.
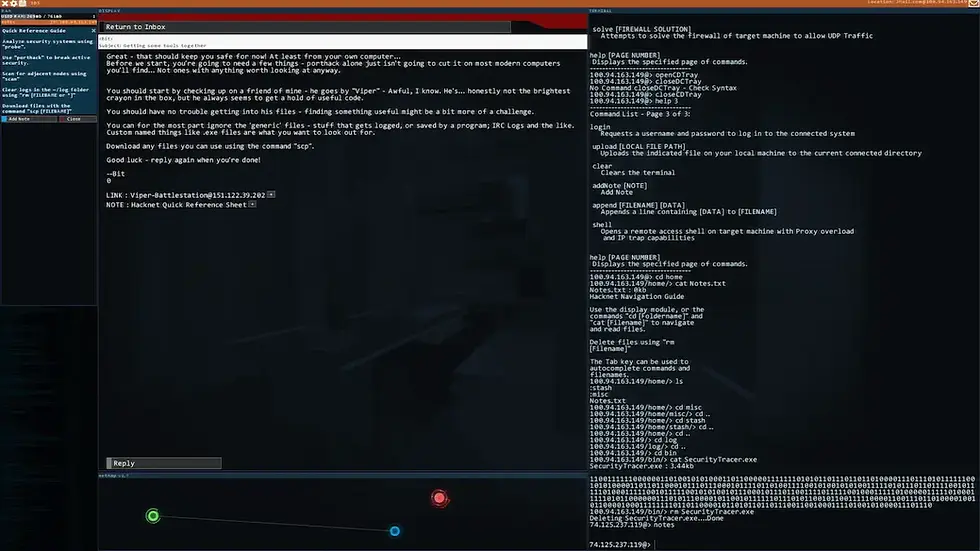
This is fun, the red node on the map is actually the email (Jmail) server I'm using. I can see its filesystem and note that there are other accounts here, but I don't have privileges to actually read their emails.


My mission instructions told me to just go for .exe program files but my snooping around in the texts gets me an IP address, I try connecting to it and it's someone's test server.

Your activities on a server leave log messages of what you did on there, like your IP address when connecting and what files you downloaded.

Bit's first 'job' for me is to go delete some log files that he was too lazy to do at the time. Come on Bit, it's like two commands!
On that server I check the logs before erasing them. Looks like 'Bit' accessed something called the Valence Dossier. It's not on the filesystem anymore - looks like they grabbed it and deleted it. Oh, I should mention that in the intro 'Bit' starts by saying that a 14-day timer has expired and he's dead, I'm getting these messages as a dead-man switch. Or so they claim.
Bit sends me to an educational server so I can learn more hacky-things.

I get Shell which I can use to control remote computers to help me overwhelm a system and firewall analysis so I can bypass firewalls.
It's also got information, and this entry on Traces seems important.

Bit left me with instructions to join a hacker group called Entropy. As a test for joining them they want me to remove some news articles from 'Slashbot' about them, and crash Slashbot.
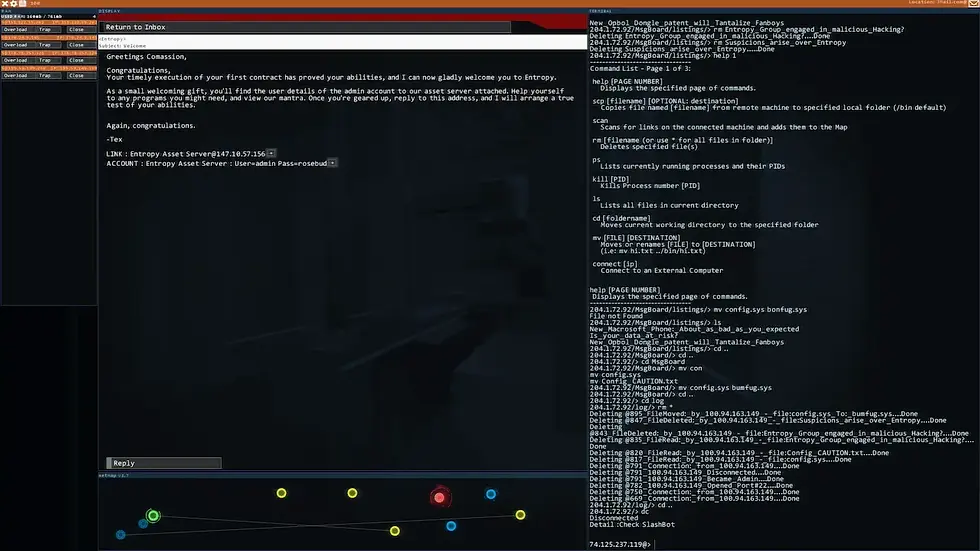
Entropy directs me to their contracts server where I can get missions. I'm enjoying that everything in this game so far - including getting missions and reading your mail - all use the main system of logging on or hacking other computers and using them.

The first mission is (assuming I'm not being deceived by a jealous rival) relatively innocent. A gamer wants to re-play a clicker game but there's no reset button, so he wants me to delete his online save data so he can start over.

So when you're hacking a server, on the left side you run programs that do a fun graphical thing and take up space in your computer's available memory.

One nutty aspect of the game is that text notes in this area use up as much memory as vertical space they require - if my computer had the Gettysburg Address open, I don't think I'd be able to run any other programs.
On Job #2 I encounter my first security measure - a trace attempt. Looks like I have to finish the job within the time limit.
Fortunately the allotted time is fairly generous - those aren't seconds counting down, each integer is actually around 4 seconds so I had several minutes for this.

Also, while the mission is to delete a mailing list that got stolen from another company, I decided to grab a copy for myself before I did so. It's encrypted and I don't know if I can decrypt it, but I figure it can't hurt to have a copy. I've been grabbing any stray files I find that look like they might be useful later and saving them on my machine. This game save file makes me want to play this game.

Another client is concerned that their X-C(om) scientist may be getting a little too familiar with alien tech.

Next mission is to delete a file that another hacker stole. This one has a much shorter countdown, but even though I'm in and out before the trace expires... they got me.
My machine reboots and the fancy interface is kaput - they messed up my computer!

Logs show they deleted my x-server.sys file and told my machine to reboot.
So this is interesting - I've seen this file on other machines, and this feels a bit more free-form than the rest of the game. I think I need to use just terminal commands to connect to another computer that still has this file (it's been present on other machines) and grab a copy from them.
Ok, got it. I grabbed extra copies of the files as backups in case this happens again.

It.. sort of worked?!?
I got a new interface, and new music (I ought to mention the music in this game is solid!).


I actually looked at the x-server.sys file and it's just a number. I tried messing with the number and using that for x-server.sys and wound up with a blank terminal again.

Uhhh... I tried changing it some more and my modified x-server.sys straight-up actually crashed the game...

I was able to fix it after restarting, I think I'll just use the green one and move on now...
A couple more small jobs and I get an invite from another group, CSEC.

After an initial straightforward test, they want me to discover the secret 11 Herbs and Spices of CFC.

I've found something that feels like a exploit - if you get access to a computer and they start tracing you, it looks like you can immediately disconnect and then reconnect, maintaining admin access so you can complete the mission but the trace is immediately terminated.
I wish the Netmap at the bottom was more organized or labeled, since it's just a bunch of circles it's not terribly helpful for connecting to a server, as there get to be more of them I have to click around to find the one I want.

I think I like the original theme I started with the best. CSEC's x-server file gives you a white interface.

It occurs to me that in a game about hacking and computer security it's very odd that you can't change your passwords.
Oh that's a bit disappointing, now that I'm a CSEC member I'm not allowed to go back and complete the rest of the Entropy contracts that I didn't finish, they want nothing to do with me!
CSEC contracts get more serious, including altering records of government systems - there's two that want you to change records of people on Death Row.

A couple contracts in I get the chance to find some decryption software. This mission is very involved and well done, I'm stuck looking at mostly encrypted files until I find one employee at the company that didn't bother to encrypt her decryption software - I grabbed that and all the encrypted files and now I'm busily decrypting / reading all the stuff they thought was safe.


Ok, time to crack open that encrypted file I got way earlier. The big reveal!

I got cocky and tried to hack the jmail server...

I didn't understand what I was supposed to do here and the game closed to represent me getting caught. On restart I took a mission that instantly does this to you and I learned that to save yourself you're supposed to hack a mainframe terminal and use it to change your IP address so you can't be located before authorities find your real address.
After a bunch of CSEC missions I get one to find out what happened to Bit.

Bit left a message on one of his servers mentioning that he was working with a company called EnTech and feeling pretty uneasy about it. This is a multi-part mission so when it's done I wait on another hacker for some follow-up info for the next mission.
So let's see what else is on the CSEC mission board... oh.
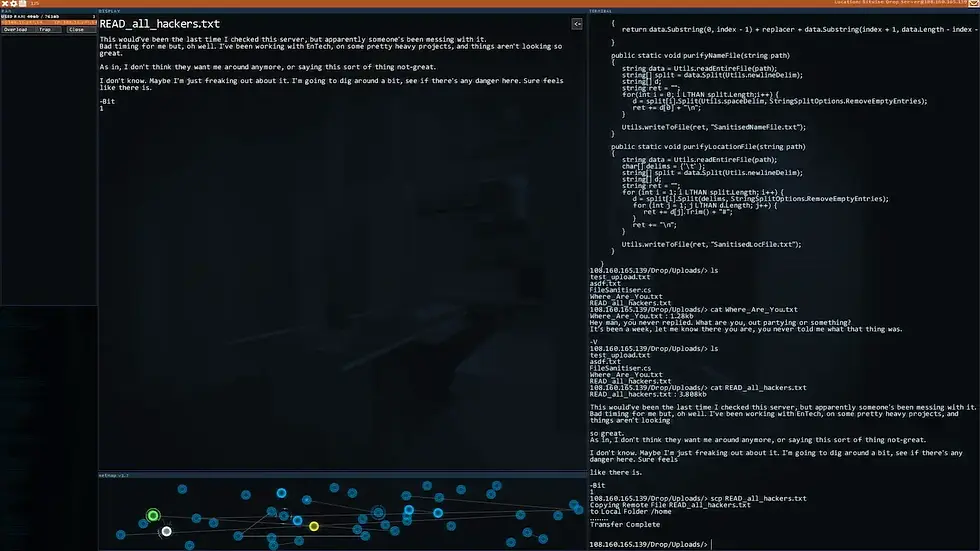
This remotely accessible pacemaker will Beep Beep no longer.

After that I get another mission on the quest to find Bit, and my benefactor hooks me up with a TraceKill program - would be great if this can just straight-up stop a trace.
It uses a ton of memory so I can't be running anything else.

Trying to find what happened to Bit is a bigger job by an order of magnitude than the others - I've already found 10 machines and a lot of them use this new security that hasn't been seen before.

Bit had a crisis of conscience over the power EnTech was assembling for itself. That power is what I'm using to hack systems right now - Hacknet, a collection of security-breaching computer programs in an easy to use interface. Bit created some of it.

Hah, I love this, an EnTech exec never intended to have Bit killed, he just wanted a goon to send a message, but the goon read a bit of slang that the exec used very differently.

What do the police charge you with if you accidentally put out a hit on someone but didn't mean to? CSEC decides to take revenge on EnTech and enlists me to help. In a time-limited mission I crack through all the security we've learned to break through so far, get on the target server, wipe their Hacknet files, wipe the logs, and destroy everything Bit built for EnTech.
One last posthumous message from Bit - he wants me to disable the program 'PortHack' that I've been using to hack everything, it's the last program you run once you crack various ports on a server with different programs.

This is a solid game with a good story but the terminal interface will not be to everyone's tastes. As for me, I've had fun with it.
Bit's last, last message is a voice recording that wants me to delete the last copy of Hacknet - the one on my computer.

I think I won the game by uninstalling it.






Comments